TeslaCrypt: how to restore encrypted files
For the uninitiated, a ransomware is a type of malware (malicious software – a computer virus) that requires a ransom to be paid to remove the limitation of access to the infected system. The most common forms of ransomware encrypt user files, asking to pay, often amounts in the order of a thousand dollars, to restore those files.
Infected files encryption is usually based on the principle of RSA encryption with public/private keypair: the public key is released to the victim, with the promise of getting the private one, needed to restore files, from the maker of the ransomware (which is the only one to know it).
The used encoding’s high number of bits (eg. 1024) makes it often impossible to self-recover the private key using distributed systems, where a series of computers attempt to identify this key starting from the public and an infected file used as sample.
Moreover, the payment is made via bitcoins and is therefore not traceable (because a peer-to-peer transaction with the beneficiary without intermediaries happens), so there is no guarantee of the fact that, in return for payment, the maker the ransomware will honor the promise to allow you to recover your files.
Some preventive recommendations to avoid entering into such a situation are:
- always make a backup of your data on another device (preferably remotely)
- use a good antivirus (Kaspersky, ESET, etc …) and keep it up to date, purchasing a license where necessary
- avoid opening files from unknown sources (suspicious email senders and/or text, untrusted web sites, etc…)
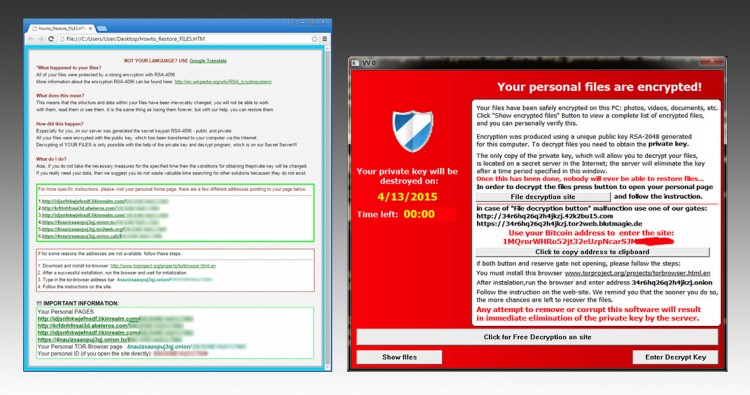
TeslaCrypt is one of ransomware that in the last months has claimed more victims: distributed in many variations, can be recognized from the image shown to the user once the files infected (which is the one shown as main picture in this article), and for the extensions given to infected files, some of which are:
- .encrypted
- .ecc
- .ezz
- .exx
- .xxx
- .ttt
- .micro
- .mp3
For several months, in particular for the last 4 extensions, there was no solution, except asking for “computational” help on some support forum, in which different users offer their computers to identify the private key that decode your files.
Starting today, however, thanks to user support known as BloodDolly, you can decrypt files with one of these four extensions using a software called TeslaDecoder, which can be downloaded here:
Beyond all the features included, let’s see how to decode a .xxx, .ttt, .micro or .mp3 infected file with this software.
Once extracted the downloaded .zip file into a folder, you must execute TeslaDecoder.exe.
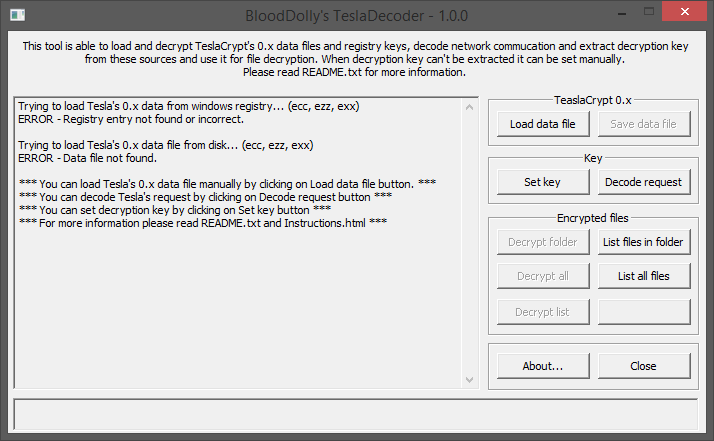
Now, click on “Set key” and, under “Extension“, select “.xxx, .ttt, .micro, .mp3” from the dropdown list.
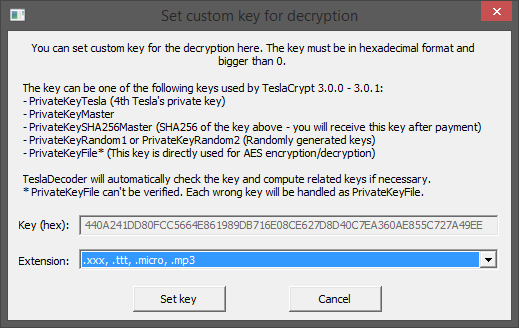
Finally, click on “Set key“. At this point, in the main screen of the software the following buttons will be enabled:
- Decrypt folder: restore files located in a specific folder
- Decrypt all: restore all infected files on your computer
- Decrypt list: restore a list of files whose names has been written by you in a text file
Personally I would use the first one to check what is restored, or the second one to avoid leaving out some file from the restore process.
Once you click on one of these three buttons you will be asked whether, as a result of decryption, you want to delete the infected file and keep only the restored one.
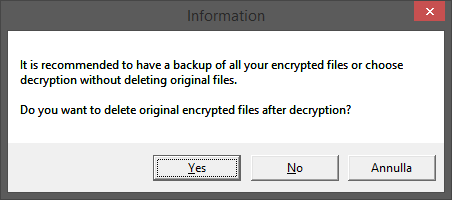
This is an important decision to make, since:
- if you decide to delete the encrypted files by clicking “Yes” and decoding fails for any reason, you have no way to retry
- if you decide to keep the encrypted files by clicking “No“, after checking for their correct decoding you will be forced to delete the infected ones manually, and when these files are scattered in different folders operation becomes very tedious and laborious.
My personal advice is to try to decode a “sample” file without deleting the encrypted version (thus by clicking on “No“), and, once verified the restored file is ok, proceed decoding the remaining ones with infected versions deletion, by repeating the operation and clicking this time on “Yes“.
Good luck!








1 Comment
Very informative blog.
I would like to thank you for the information.